Introduction
In today’s digital landscape, businesses, and individuals increasingly rely on cloud computing to store and process their data. The cloud offers numerous advantages, such as scalability, flexibility, and cost-effectiveness. However, with these benefits come inherent security risks. Protecting sensitive data in the cloud is paramount, as any breach can result in financial losses, reputational damage, and regulatory non-compliance. In this article, we will delve into the best practices for cloud security, equipping you with the knowledge to safeguard your data in the cloud.
- Understand the Shared Responsibility Model:
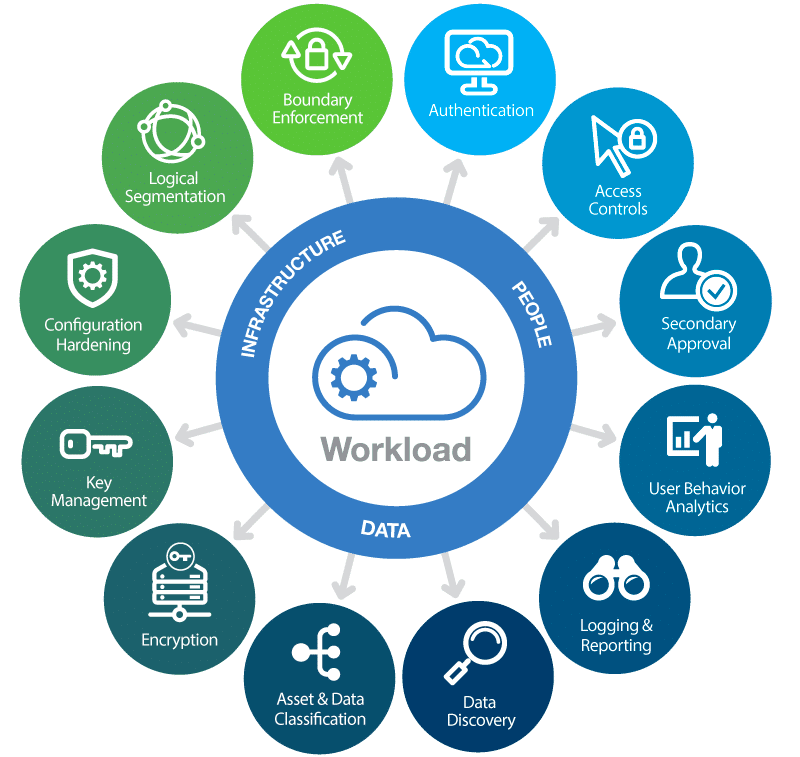
Cloud security is a shared responsibility between cloud service providers (CSPs) and cloud users. CSPs are responsible for securing the infrastructure, while customers are responsible for securing their data and applications. It is crucial to understand this model and know your role in securing your cloud environment. - Implement Strong Access Controls:
Proper access control is vital to prevent unauthorized access to your data. Adopting the principle of least privilege ensures that users are granted the minimum necessary access rights to perform their tasks. Utilize strong and unique passwords, and multi-factor authentication (MFA), and regularly review and revoke access permissions to minimize the risk of unauthorized access. - Encrypt Your Data:
Encrypting data before storing it in the cloud adds an additional layer of protection. Utilize encryption techniques such as transport layer security (TLS) for data in transit and encryption at rest for data stored in the cloud. Encryption ensures that even if data is compromised, it remains unreadable without the decryption keys. - Implement Robust Network Security:
Cloud environments require strong network security controls. Employ firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) to monitor and filter network traffic. Segment your network to isolate sensitive data and ensure that communication between different segments is properly secured. - Regularly Patch and Update Systems:
Cloud service providers regularly release security patches and updates for their platforms. It is crucial to promptly apply these updates to ensure that known vulnerabilities are addressed. Implement an effective patch management process to stay up to date with the latest security fixes. - Perform Regular Security Audits and Assessments:
Regularly assess your cloud environment’s security posture to identify vulnerabilities and potential risks. Conduct penetration testing, vulnerability scanning, and security audits to uncover any weaknesses. Address the identified issues promptly and ensure that security assessments are performed periodically. - Backup and Disaster Recovery:
Implement a robust backup strategy to protect against data loss and enable quick recovery in the event of a breach or disaster. Regularly back up your data and verify the integrity of backups. Test your disaster recovery plan to ensure it functions as expected during critical situations. - Monitor and Analyze Logs:
Enable logging and monitoring capabilities provided by your cloud service provider. Monitor logs for suspicious activities, such as unauthorized access attempts, unusual data transfers, or configuration changes. Implement a centralized log management system to collect and analyze logs from different cloud services for timely threat detection and incident response. - Educate and Train Users:
One of the weakest links in cloud security is often human error. Educate your employees and users about best practices for cloud security. Train them to recognize phishing attempts, use strong passwords, and follow proper data handling procedures. Foster a culture of security awareness throughout your organization. - Stay Updated on Cloud Security:
Cloud security is a constantly evolving field. Stay updated with the latest trends, best practices, and security threats in the cloud computing industry. Regularly review your security measures and adjust them as necessary to align with emerging threats and technologies.
Conclusion
Securing your data in the cloud requires a multi-layered approach. By following these best practices, you can significantly enhance your cloud security posture and mitigate the risk of data